Facebook ads push Android adware with 7 million installs on Google Play

Several adware apps promoted aggressively on Facebook as system cleaners and optimizers for Android devices are counting millions of installations on Google Play store.
The apps lack all of the promised functionality and push advertisements while trying to last as long as possible on the device.
To evade deletion, the apps hide on the victim’s device by constantly changing icons and names, masquerading as Settings or the Play Store itself.

The adware apps abuse the Contact Provider Android component, which enables them to transfer data between the device and online services.
The subsystem is called every time a new app is installed, so the adware might be using it to initiate the ad-serving process. To the user it may look like the ads are pushed by the legitimate app they installed.
Researchers at McAfee discovered the adware apps. They note that users don’t have to launch them after installation to see the ads because the adware initiates itself automatically without any interaction.
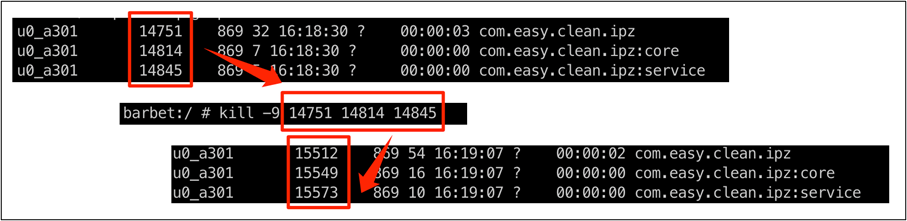
The first action from these annoying apps is to create a permanent service for displaying the advertisements. If the process is “killed” (terminated), it re-launs immediately.
The following video shows how the name and icon of the adware changes automatically and how the ad-serving occurs without any interaction from the user.
Millions of downloads on Google Play
As McAfee comments in the report, users are convinced to trust the adware apps because they see a Play Store link on Facebook, leaving little margin for doubt.

This has been in unusually high download numbers for the particular type of applications, as shown in the list below:
- Junk Cleanercn.junk.clean.plp, 1M+ downloads
- EasyCleanercom.easy.clean.ipz, 100K+ downloads
- powerdoctor, com.power.doctor.mnb, 500K+ downloads
- Super Cleancom.super.clean.zaz, 500K+ downloads
- Full Clean -Clean Cache, org.stemp.fll.clean, 1M+ downloads
- Fingertip Cleanercom.fingertip.clean.cvb, 500K+ downloads
- Quick Cleanerorg.qck.cle.oyo, 1M+ downloads
- Keep Cleanorg.clean.sys.lunch, 1M+ downloads
- Windy Cleanin.phone.clean.www, 500K+ downloads
- Carpet Cleanog.crp.cln.zda, 100K+ downloads
- Cool Cleansyn.clean.cool.zbc, 500K+ downloads
- Strong Cleanin.memory.sys.clean, 500K+ downloads
- Meteor Cleanorg.ssl.wind.clean, 100K+ downloads
Most affected users are based in South Korea, Japan, and Brazil, but the adware has unfortunately reached users worldwide.
.png)
The adware apps are no longer available on the Play Store. However, users that installed them have to remove them manually from the device.
System cleaners and optimizers are popular software categories despite the low benefits they provide. Cybercriminals know that a large number of users would try such solutions to prolong the life of their devices and often guise malicious apps as such.